we're currently in the process of putting together our own server Firewall/Router. We were going to use a dedicated solution from someone like Juniper or Watchguard, but it is going to be a lot more cost-effective if we use a server machine we were planning to get already, instead.
About us: We're a website that is going to have two servers behind the Firewall/Router Server (a web server and a database server). All three servers are going to be running Windows Server 2008 R2 x64.
Excuse the crudity of my diagram (I know it's not even close to being technically correct, but it hopefully makes our topology a little clearer)...
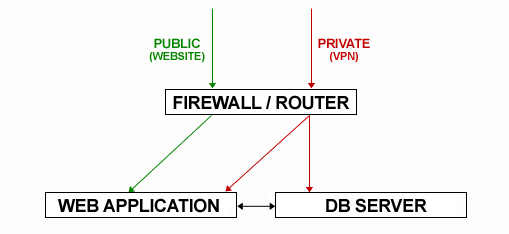
#1 ROUTING
We are using RRAS to configure our routing. At the moment this is configured to give our Web App server internet access (through RRAS's NAT) but I need to set up port forwarding so that any request to port 80 is sent directly to the Web App server.
#2 FIREWALL
Would Windows Advanced Firewall do our required job acceptably? (I imagine the answer to this is yes.)
#3 VPN
Setting up a VPN has been a pain so far (certificates are annoying!). Every tutorial I've seen seems to have a DNS and DHCP roles running on their VPN machine... why is this? Are they both necessary or can I bin them?
Overall
Are the any more tips on how to configure this server for our needs?
Thanks for any advice. I'm sorry if this is a really badly asked question! (There is a bounty, at least :)
You can use RRAS for firewalling, NAT and VPN, so, yes, you can give a single public IP address to your Windows Server 2008 firewall and have it route traffic for all your internal network and forward specific ports (f.e. 80) to your internal servers, and you can also have it act like a VPN server (PPTP and/or L2TP). RRAS has been around since Windows 2000, and it does its job quite nicely for simple setups.
It isn't a full firewall/proxy solution, though; you can't define fine-grained policies, it doesn't do any web proxying (be it straight or reverse), it can't filter traffic at the application level and it doesn't log network traffic for further analysis.
In short: yes, RRAS can do anything you need, simply and somewhat crudely; but it isn't a full-blown network access and security solution like ISA or TMG.
I just set up something pretty similar about an hour ago. Windows Server 2008 R2 is a fully viable solution for what you're doing.
I agree with the comments so far about using ISA for the firewall. Windows firewall could work but it's pretty basic and doesn't have any IDS or filtering. ISA is the way to go if you can, otherwise Windows Firewall is ok as a stepping stone.
For your VPN, no, DNS and DHCP don't need to be on the same server as RRAS. DNS can be anywhere, and DHCP just needs to be in the internal subnet.
For your internal IPs, they can originate on the firewall/router server, so the top left line in your diagram is really a line inside of the green line. Use VPN to connect to the firewall/router/vpn server which will assign an internal IP.
For the database server, just give it an internal IP and it will only be accessible from the inside.
On the router server's internal NIC, assign a x.x.x.1 (i.e. 10.0.0.1) IP and use that as your gateway for your internal NIC on the web server and for your database server. That will give you the internal network and routing.
Also, if you install RD Gateway Server, you can RDP to your inside computer from outside the network too.
If you are set on using a Server2008 box as your firewall, then you may want to consider using ISA.
To be honest why not go with a mid-low end Small business router from linksys. I use the RV042 in that exact setup. I have one IP address that is forwarded to the Webserver (using NAT) on 80 and 443 and the router is a VPN server as well just using the Windows VPN client. It's about $200 then your server is actually physically removed from the internet should something on the server's software firewall be accidently turned off it won't be sitting exposed on the internet.
We use Kerio Winroute Firewall on our windows servers. It doesn't do reverse proxy at all but as for everything else it is pretty well supported with features. We've been using it for 8/9 years through the various versions and currently it is very good. It is also cheaper than ISA and much easier to configure.
As for the reverse proxy, we've not needed that yet but would be interested to find out what you do in the end if you need to. We have so far got around it as we have a block of IP addresses so just map those to different internal servers.
Let me know if you need any help with configuring it at all.
1) About routing Yes it all can be simply routed to your IIS with RRAS, you only need to set up proper DNS A records and make several clicks in RRAS snap-in and also you need to setup IIS to catch up proper headers and ports.
2) It is possible to work without firewall but of course it will decrease security. It is possible to put simple FreeBSD, Linux or anything else based boundary firewall, or simple hardware firewall.
3) Windows 2008 offers great SSTP, besides PPTP and L2TP, VPN tunnels, which doesn't depend on GRE protocol and work everywhere. But do you really need VPN tunnels? Server 2008 also offers great feature TS RemoteApp which is more securely, because doesn't offer full access to server's network, but only to a particular application.
Do you plan server to host internal web recources as well?
I had a similar problem of yours. A gentleman in this forum recommended me to use Astaro Security Gateway.
I grabbed their free home license and played for a while with the software. By the end of the day (actually night), I was able to configure a Pentium 4 machine to act as a successful firewall and a replacement for two separate routers.
Now I run a web server that serves over two WAN IP addresses (with uplink load balancing) and the internal traffic is redirected to the local IP of the server without travelling through the internet.
The advantage of Astaro is that you have granular controls of each and every packet movement in your network. You may have to try it first.
You didn't say what platform you're looking at, so I'm going to recommened m0n0wall.
It's an all-inclusive repackaging of FreeBSD for use as a firewall/router/etc.
EDIT
updating based on comments from Django, I thought the Win2k8 servers were to be BEHIND the firewall, not upon which to INSTALL the firewall
With that being the case, my initial recommendation of m0n0wall doesn't make any sense :)
If you change your mind, though, it may still :)